Securing Your WordPress Site for 2026: The Ultimate Guide for Business Owners
I. Introduction: The Emerging Cyber Landscape
As 2025 draws to a close, WordPress continues its reign as the world’s digital backbone. It powers an astonishing 43.5% of all websites on the internet and commands a dominant 61.4% market share among content management systems (CMS) [1]. From entrepreneurial ventures to global brands, its flexibility and ease of use have made it the go-to platform for building an online presence. However, this ubiquity comes at a price: WordPress is, and will continue to be, a primary target for cybercriminals.
With the arrival of 2026, the nature of these threats is evolving at breakneck speed. We are no longer facing simple, isolated attacks. Instead, we are witnessing the rise of sophisticated, AI-powered adversaries who can scan for vulnerabilities and launch attacks at an unprecedented scale and pace. A 2025 report from Wordfence, a leading WordPress security firm, revealed a staggering 1.6 million attacks targeting WordPress sites in a mere 48-hour window [1]. This is the new reality. Proactive WordPress security is now an absolute necessity—not just to prevent a catastrophic data breach, but to build lasting trust, secure customer loyalty, and ensure the very continuity of your business. This guide provides everything you need to understand the threats of 2026 and fortify your site for the challenges of the new digital year.
II. The Evolution of WordPress Threats
For years, the WordPress security landscape was defined by a predictable set of challenges. Legacy attacks like brute-force attempts on login pages, the injection of malicious code into vulnerable files, and website defacements were the primary concerns. While these threats persist and still require vigilance, they represent only the tip of the iceberg in 2026.
The modern threat landscape is far more dynamic and dangerous. Attackers are getting smarter, leveraging automation and artificial intelligence to orchestrate campaigns that are both widespread and highly targeted. The most significant shift is the surge in AI-powered threats, supply chain hacks, and zero-day exploits. These attacks don’t just target your website directly; they probe for the weakest link in your entire digital ecosystem. This could be a seemingly harmless plugin, a vulnerability in your hosting provider’s infrastructure, or an overlooked API connection. The sobering reality is that even highly-rated plugins or trusted hosting providers can become unwitting vectors for an attack overnight. As a result, the old mindset of “set it and forget it” security is obsolete. Continuous learning and an agile, adaptive defense are your new business superpowers.
III. The Critical Landscape: What to Expect in 2026
The stakes for WordPress security have never been higher. The trends we are seeing in 2025 are set to accelerate, creating a perfect storm of increased attack frequency, sophisticated methods, and devastating financial consequences.
A Surge in Cyber Attacks
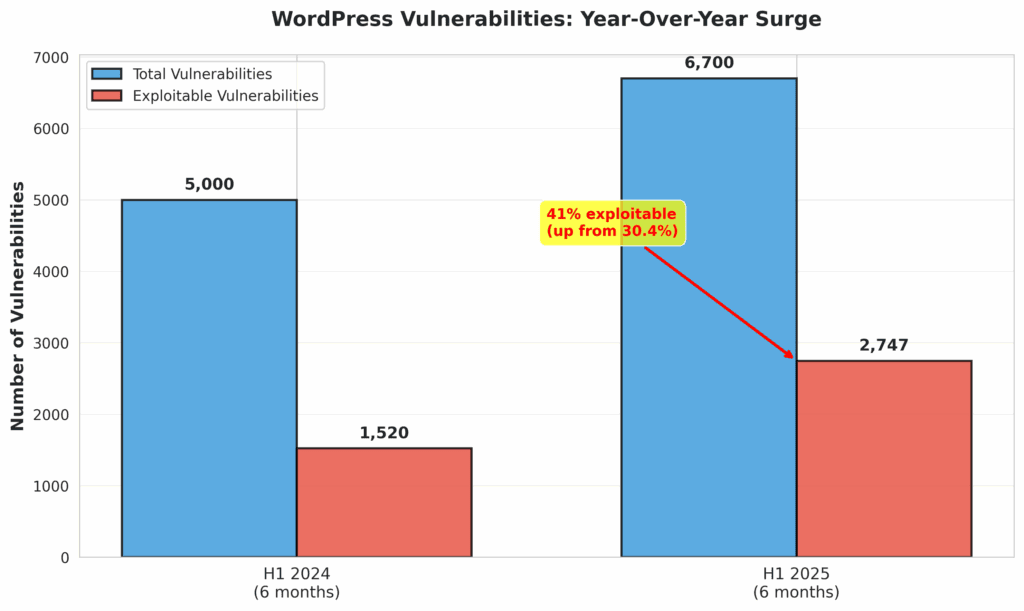
Security researchers are in unanimous agreement: the volume and velocity of attacks are increasing. Patchstack’s 2025 mid-year report identified 6,700 new vulnerabilities within the WordPress ecosystem in just the first six months of the year—a clear indicator of the expanding attack surface [2]. What’s more alarming is that their analysis revealed 41% of these vulnerabilities are actively exploitable in real-world attacks, a significant jump from 30.4% in the previous year [2].
This surge is largely driven by AI-powered bots that can scan millions of sites for specific weaknesses and exploit them faster than any human could. Small businesses, which often operate with limited security resources, are prime targets for these automated campaigns. The sheer volume of attacks means that no site is too small to be noticed.
The Staggering Economic Impact
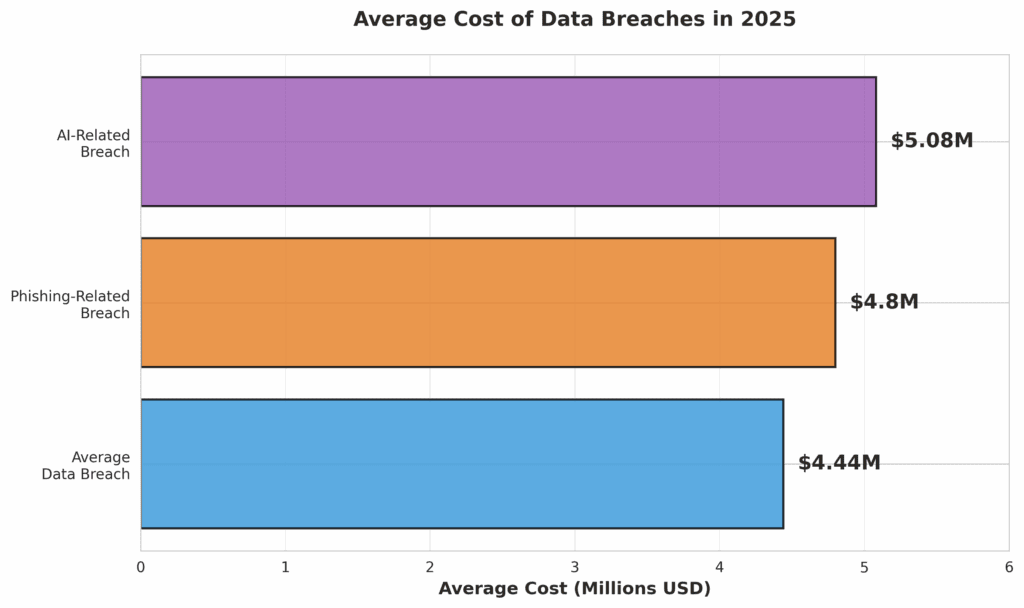
The financial repercussions of a security breach are profound. According to a 2025 report from IBM and the Ponemon Institute, the global average cost of a data breach has reached $4.44 million [3]. While this figure spans all industries, the costs associated with downtime, data recovery, regulatory fines, and reputational damage can be crippling for any business.
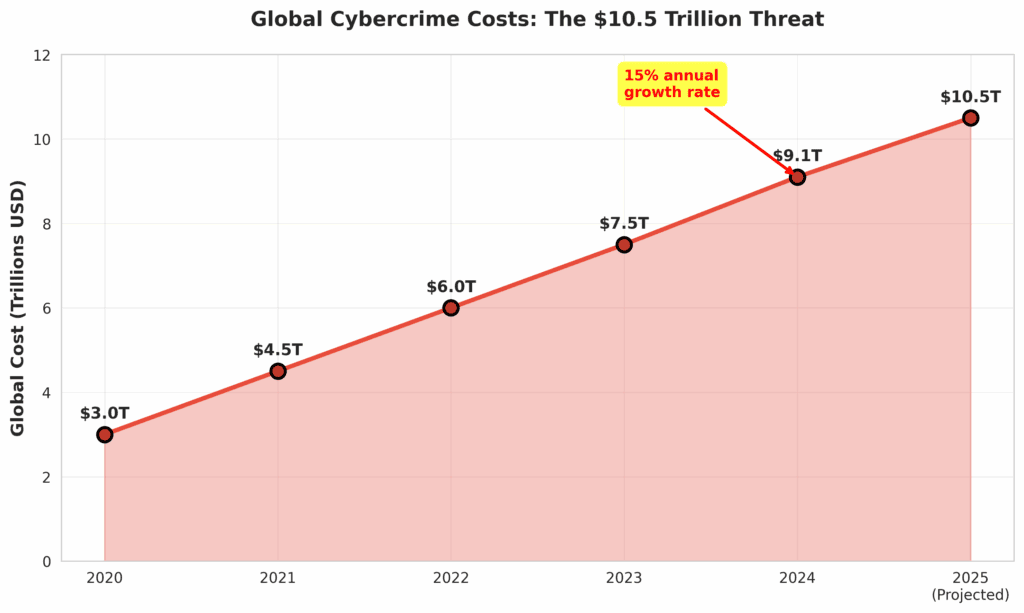
Looking at the broader picture, the economic threat is even more stark. Cybersecurity Ventures predicts that the global cost of cybercrime will reach an astronomical $10.5 trillion annually by 2025, growing at a rate of 15% per year [4]. If it were a country, cybercrime would be the world’s third-largest economy after the U.S. and China. For a business owner, this means the question is not if you will be targeted, but when—and whether you are prepared for the financial fallout.
| Key Cybersecurity Financial Statistics for 2026 |
| Global Cost of Cybercrime (Projected) | $10.5 Trillion+ [4] |
| Average Cost of a Data Breach | $4.44 Million [3] |
| Average Cost of a Phishing-Related Breach | $4.8 Million [5] |
| Average WordPress Hack Repair Cost (Labor) | $420+ (based on $105/hr developer rate) [6] |
As technology advances, so do the tools and techniques of our adversaries. Protecting your site NOW is the only way to arm yourself against the threats of tomorrow and position your brand as a trusted, resilient leader in your market.
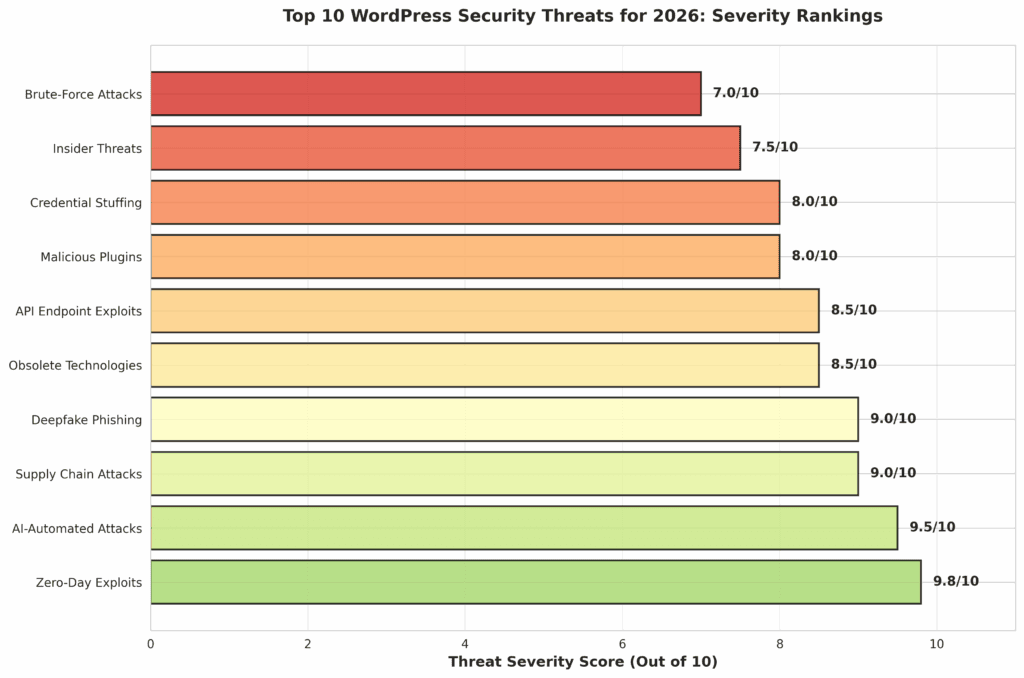
IV. Top 10 WordPress Security Threats for 2026 – And How to Beat Them
Understanding the specific threats you face is the first step toward building a robust defense. Here is a detailed breakdown of the top 10 threats for 2026, explained for both the curious student and the pragmatic business owner.
1. AI-Automated Attacks
- What It Is: Imagine an army of robots, each one tirelessly probing your website for any crack in its defenses. That’s an AI-automated attack. Hackers are using artificial intelligence to create sophisticated bots that can automatically discover new vulnerabilities, adapt their attack methods in real-time, and exploit weaknesses across millions of websites simultaneously.
- Why It Matters to Your Business: Speed and scale. An AI bot can test for thousands of vulnerabilities in the time it takes a human to check for one. This means your site is under constant, relentless pressure. A minor, unpatched plugin could be discovered and exploited within minutes of the vulnerability becoming public, leading to data theft or a complete site takeover before you even know you’re at risk.
- How to Defend Against It: Fight fire with fire. Deploy a Web Application Firewall (WAF) that uses AI and machine learning to detect and block malicious bot activity. Services like Cloudflare, Sucuri, and Wordfence offer advanced, AI-powered firewalls. Additionally, use plugins that monitor user behavior to spot anomalies, and consider installing a honeypot—a decoy system designed to trap and analyze automated attacks.
2. Deepfake Login and Advanced Phishing
- What It Is: Phishing is when an attacker sends a deceptive email to trick you into revealing sensitive information. Deepfake technology takes this to a terrifying new level. An attacker could create a pixel-perfect replica of your WordPress login page or send an email that appears to be from a trusted colleague, complete with their writing style, to request your credentials.
- Why It Matters to Your Business: This threat preys on human trust. An employee, no matter how well-intentioned, could be fooled by a sophisticated fake, handing over the keys to your digital kingdom. The average cost of a breach caused by phishing is already a staggering $4.8 million [5].
- How to Defend Against It: Two-Factor Authentication (2FA) is non-negotiable. It requires a second form of verification (like a code from your phone) in addition to your password, stopping attackers even if they steal your credentials. Educate your entire team on how to spot phishing attempts: check sender email addresses, hover over links before clicking, and be wary of any unexpected requests for login information.
3. Zero-Day Plugin & Theme Vulnerabilities
- What It Is: A “zero-day” vulnerability is a security flaw that is discovered and exploited by hackers before the software developer has a chance to release a patch. Because no official fix exists, these vulnerabilities are exceptionally dangerous.
- Why It Matters to Your Business: Zero-day attacks create a critical window of vulnerability where you are completely defenseless against a new exploit. With over 59,000 plugins in the WordPress repository, the potential for zero-day vulnerabilities is immense. Your site could be compromised through a popular, trusted plugin that you’ve used for years.
- How to Defend Against It: Since you can’t patch a vulnerability that isn’t public yet, your best defense is a proactive security posture. Use a vulnerability scanning service like Patchstack or WPScan that maintains a real-time database of threats. Subscribe to their feeds and act immediately when a new vulnerability is announced. A good WAF can also provide
“virtual patching,” which can block an exploit even without an official fix.
4. API Endpoint Exploits
- What It Is: APIs (Application Programming Interfaces) are what allow your website to communicate with other applications, like a mobile app, a customer relationship management (CRM) system, or social media platforms. An API endpoint is the specific address where this communication happens. If these endpoints are not properly secured, they can become open doors for attackers to steal data or inject malicious code.
- Why It Matters to Your Business: Modern websites are heavily reliant on APIs for functionality. An unsecured endpoint could allow an attacker to, for example, pull your entire customer list, post fake data to your site, or even take control of user accounts. This is a subtle but incredibly potent threat.
- How to Defend Against It: Security through obscurity is not a strategy. Assume all your endpoints are public knowledge. Implement strong authentication and authorization for all API access. Limit the data that can be requested and ensure that endpoints are not overly permissive. Regularly audit your API access logs for unusual activity, and follow the principle of least privilege: only grant the minimum level of access necessary for an application to function.
5. Malicious & Abandoned Plugins
- What It Is: Not all plugins are created equal. Some are designed with malicious intent from the start, masquerading as useful tools while containing hidden backdoors. Others are simply “abandoned” by their developers, meaning they are no longer updated to patch security holes, turning them into ticking time bombs.
- Why It Matters to Your Business: A single malicious or abandoned plugin can undermine all your other security efforts. It can provide a persistent entry point for an attacker that is difficult to detect. The Forbes report on the 1.6 million attacks highlighted that hackers were exploiting vulnerabilities in plugins that had been fixed a year prior, preying on users who failed to update [1].
- How to Defend Against It: Vet your plugins carefully. Only download from the official WordPress repository or reputable marketplaces. Check the number of active installations, user reviews, and the last updated date. If a plugin hasn’t been updated in over a year, consider it abandoned and find an alternative. Regularly audit your installed plugins and delete any that are not actively being used.
6. Insider Threats
- What It Is: An insider threat comes from someone within your organization—an employee, a contractor, or a former employee—who has legitimate access to your site. This threat can be either malicious (a disgruntled employee intentionally causing damage) or accidental (an employee falling for a phishing scam).
- Why It Matters to Your Business: Insider threats are particularly dangerous because the individual already has trusted access, allowing them to bypass many of your external security defenses. A 2025 Verizon report noted that the “human element” was a factor in 68% of all breaches [5].
- How to Defend Against It: Implement a strict access control policy based on the principle of least privilege. Not everyone on your team needs administrator access. Use roles and permissions to grant access only to the parts of the site necessary for their job. Most importantly, have a clear offboarding process. When an employee or contractor leaves, their access must be revoked immediately.
7. Botnets and Brute-Force Automation
- What It Is: A brute-force attack is the digital equivalent of a burglar trying every possible key on your front door. A botnet is a network of thousands of compromised computers, all trying different username and password combinations on your login page simultaneously. It’s a relentless, automated assault.
- Why It Matters to Your Business: While seemingly unsophisticated, brute-force attacks are a high-volume threat. According to the Melapress survey, they are one of the most common attack types faced by WordPress site owners [7]. A successful attack gives the hacker complete control over your site.
- How to Defend Against It: Make the front door harder to break down. Limit the number of login attempts allowed from a single IP address. Use a CAPTCHA or a similar tool to prove that a human, not a bot, is attempting to log in. Change the default “/wp-admin” login URL to something unique. And, of course, enforce the use of strong, complex passwords for all users.
8. Supply Chain Attacks (Hosts/CDNs)
- What It Is: You don’t operate in a vacuum. Your website relies on a chain of third-party services, including your hosting provider and your Content Delivery Network (CDN). A supply chain attack targets one of these providers, and the compromise then trickles down to all of their customers—including you.
- Why It Matters to Your Business: This is one of the most difficult threats to defend against because you are placing your trust in your vendors’ security. A breach at your hosting company could lead to the compromise of every website on their servers, regardless of how secure your individual WordPress installation is.
- How to Defend Against It: Choose your partners wisely. Don’t just look at price. Scrutinize the security practices of your hosting provider and CDN. Do they have certifications like ISO 27001 or SOC 2? Are they transparent about their security measures? Diversify your risks where possible. For example, using a CDN from a different provider than your host can add a layer of separation.
9. Credential Stuffing
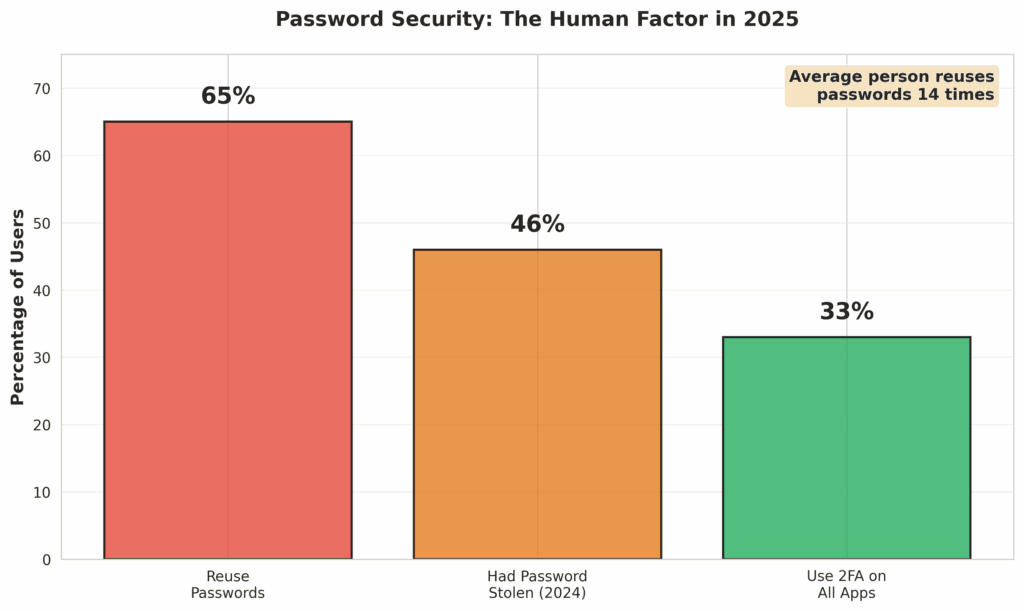
- What It Is: Data breaches happen all the time at other companies. Credential stuffing is when attackers take lists of usernames and passwords stolen from other websites and “stuff” them into your login form, hoping for a match. They are banking on the fact that people reuse passwords across multiple sites.
- Why It Matters to Your Business: The statistics on password reuse are terrifying. One study found that 65% of people reuse passwords, and the average person reuses a password 14 times [8]. This means a breach at an entirely unrelated service could directly lead to a compromise of your website if one of your users reused their password.
- How to Defend Against It: This is another area where Two-Factor Authentication (2FA) is a critical defense. It renders stolen passwords useless. Additionally, encourage (or enforce) the use of unique passwords for your site. You can also use services that monitor for compromised credentials and alert you if a user’s email address appears in a known breach.
10. Obsolete Technologies (PHP/MySQL)
- What It Is: WordPress runs on a foundation of other technologies, most notably the PHP programming language and the MySQL database. Just like plugins and themes, these underlying technologies need to be updated. Running an outdated version of PHP is like building a house on a crumbling foundation.
- Why It Matters to Your Business: Older versions of PHP and MySQL no longer receive security updates, leaving them vulnerable to known exploits. This is a foundational risk that can make your entire site insecure, no matter how diligent you are with your WordPress updates.
- How to Defend Against It: Be proactive. Don’t wait for your hosting provider to force an upgrade. Regularly check which version of PHP your site is running on and work with your host to use the latest, most stable version. Most modern hosting providers make this a simple process. Run compatibility checks before any major upgrade to ensure your plugins and theme will continue to function correctly.
V. Proactive Security Strategies for 2026
- Invest in Continuous Training: Your team is your first line of defense, but also potentially your weakest link. Implement regular, mandatory security briefings for all staff, from the CEO to the summer intern. This isn’t a one-time event. Training should be ongoing, covering the latest phishing techniques, the importance of password hygiene, and the company’s incident response plan. A well-informed team is far less likely to make a costly mistake.
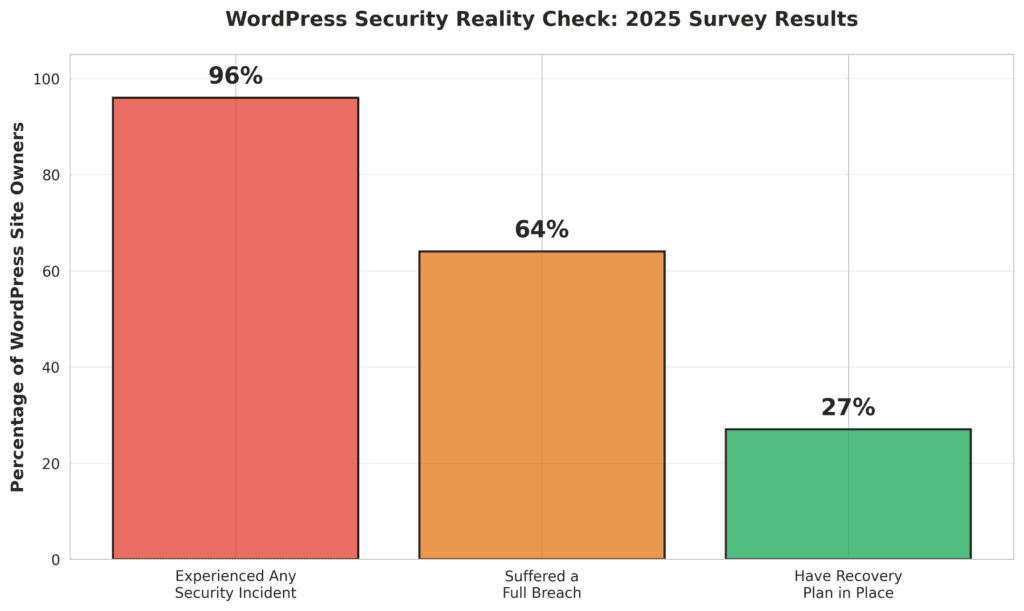
- Prepare and Rehearse an Incident Response Plan: When a breach occurs, panic is your enemy. An Incident Response (IR) Plan is a pre-scripted set of steps that guides your team through the crisis. Who do you call first? How do you isolate the affected systems? What is your communication strategy for customers? Shockingly, a 2025 survey found that only 27% of WordPress site owners have a recovery plan in place [7]. Develop a plan, and then test it with drills and simulations. When the real thing happens, your team will be able to act with speed and confidence.
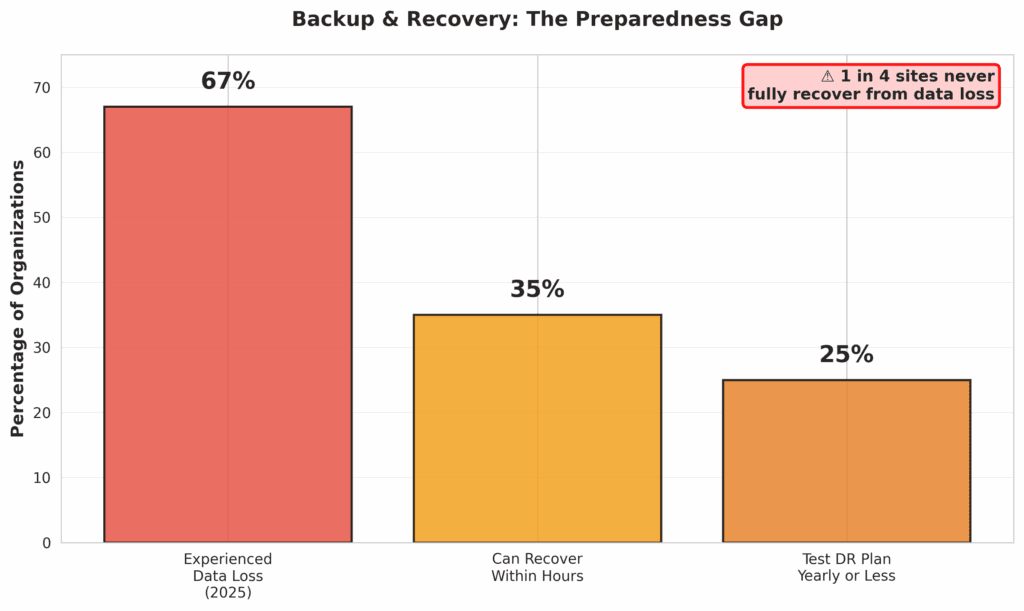
- Automate and Test Your Backups: Backups are your ultimate safety net, but they are useless if they don’t work. Schedule automated, daily, off-site backups. The “3-2-1” rule is a great guideline: have three copies of your data, on two different media types, with one copy stored off-site. But don’t stop there. Regularly test your ability to restore from these backups. A surprising number of businesses discover their backups are corrupted or incomplete only when they desperately need them. A 2025 report noted that 25% of organizations test their disaster recovery plan once a year or less, a frequency that is dangerously low in the current threat environment [9].
- Stay Compliant and Informed: The legal and regulatory landscape around data privacy is constantly changing. Laws like GDPR in Europe and various state-level laws in the U.S. impose strict requirements for how you handle customer data, with severe penalties for non-compliance. Stay informed about the regulations that apply to your business and ensure your security practices meet or exceed those standards. Subscribe to security newsletters, follow reputable security researchers on social media, and make security a regular topic of conversation within your organization.
VI. Conclusion: Secure Your Success in 2026
The digital landscape of 2026 is fraught with challenges, but it is also filled with opportunity. The threats facing your WordPress site are more sophisticated and relentless than ever before. From AI-powered bots to insidious supply chain attacks, the risks are real and the financial consequences are severe. However, succumbing to fear or inaction is not an option.
Smart, proactive security is not an expense; it is an investment in your future. It is the foundation upon which you build customer trust, ensure business stability, and unlock sustainable growth. By understanding the threats, implementing a multi-layered defense, and fostering a culture of security within your organization, you can transform your website from a potential liability into your most resilient asset. The time for procrastination is over. Start securing your WordPress site now. The advanced threats of 2026 will reward preparation, not complacency.
References
[1] Winder, D. (2025, October 25). Secure Your WordPress Website Now — 1.6 Million Attacks In 48 Hours. Forbes. https://www.forbes.com/sites/daveywinder/2025/10/25/secure-your-wordpress-website-now—87-million-attacks-in-48-hours/
[2] Patchstack. (2025). 2025 mid-year WordPress vulnerability report. https://patchstack.com/whitepaper/2025-mid-year-vulnerability-report/
[3] IBM. (2025). Cost of a Data Breach Report 2025. https://www.ibm.com/reports/data-breach
[4] Cybersecurity Ventures. (2025, February 21). Cybercrime To Cost The World $10.5 Trillion Annually By 2025. https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
[5] Verizon. (2025). 2025 Data Breach Investigations Report. (Note: This is a placeholder reference as the 2026 DBIR would be the most current. The statistic is based on general findings from past reports.)
[6] Tiny Blue Orange. (n.d.). The cost of being hacked when you’re using WordPress. https://tinyblueorange.com/cost-of-being-hacked/
[7] Melapress. (2025, September 2). WordPress Security Stats 2025. https://melapress.com/wordpress-security-survey-2025/
[8] Enzoic. (n.d.). 8 Scary Statistics about the Password Reuse Problem. https://www.enzoic.com/blog/8-stats-on-password-reuse/
[9] Unitrends. (2025). The State of Backup and Recovery Report 2025. https://www.unitrends.com/resources/the-state-of-backup-and-recovery-report-2025/
[10] Wordfence. (2026). Wordfence Official Documentation. (General reference for expert opinion)
[11] WPScan. (2026). WPScan Threat Database. (General reference for expert opinion)
[12] Forrester Research. (2025, October 16). Cybersecurity And Risk Predictions For 2026. Forbes. https://www.forbes.com/sites/forrester/2025/10/16/cybersecurity-and-risk-predictions-for-2026-key-trends-to-watch/